Everybody nowadays prefers to work in remote systems where files are consistently being shared within the organization and within the industry. Some of the activities are quite unavailable in this case which is the main reason that everybody has to focus on the technicalities of hashing algorithms so that overall businesses will be functioning very smoothly. Being very clear about the basics of credentials is definitely important in this case and in many organizations, the username and password will be present in the table in the database. Whenever somebody attempts to log in, the system will check the username and will compare the password entered by the user so that everything will be streamlined accordingly without any problem. Hence, in this case, every organisation should become very much aware of the basics of hashing algorithms so that they can competitively survive in today’s world without any problem
What do you mean by hashing algorithms?
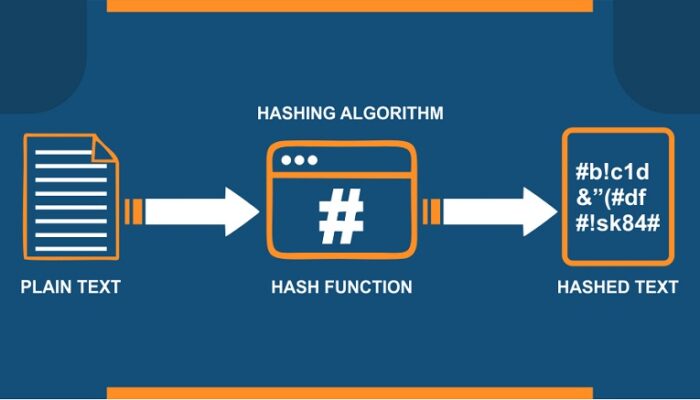
Hashing algorithms are basically a fundamental component of cryptography and will refer to the basics of chopping the data into smaller and makes pieces which makes it very difficult for the end user to go back to the original state. This particular functioning will be basically an algorithm that will generate the fixed length result and further will provide people with specific input data. It will be quite different from the concept of encryption but will provide people with the best opportunity to deal with password security without any problems in the whole process. Hashing algorithms can be very well used by the organization for password storage, integrity checking, digital signatures, and authentication systems without any issue.
Following are some of the basic points that ultimately help in making any function of ideal hashing algorithms function:
- Always focus on behaving as a one-way function: It is impossible to go back to the original state once the concept of hashing algorithms has been subjected in terms of basic implementation. Ultimately to get the specific result, ideal functions have to be implemented so that there is no chance of any kind of hassle and the initial inputs will be very well sorted out. So, in this particular case, people will definitely need to have a good understanding of that particular system which will be behaving as a way function
- It should be based upon the use of the avalanche effect: Any particular input will be definitely helpful in providing people with a particular output and even minor changes in the industry will definitely lead to significant changes in the output. So, the ideal function will be the one that will be further based upon the avalanche effect and will provide people with the best level of support at all times.
- It should be very fast in terms of computing: For any element of given input data, getting the results within the second is definitely important so that everything will be very well sorted out and further the things will be built strongly. In this case, people will be definitely able to carry out the basic tech charities without any problem and the overall limit of speed will be very high without any issues.
- It should not be based upon any kind of element of collision: The output of two parameters will never be the same which is the main reason that people need to have a good understanding of the basic technicalities in the industry so that element of pollution will be perfectly eliminated and things are perfectly sorted out without any issue
- It should be deterministic: The output of one input parameter has to be the same respective of whenever the individuals will be checking and how many times it will be used. So, this point will be especially coming in handy when multiple people will be verifying things at different points in time further people always have to focus on the basic technicalities in the industries so that everything will be done in the right direction without any practical difficulty at any point in time.
Some of these significant details that you need to know about the multiple types of hashing algorithms available in the industry have been very well explained as follows
- MD5: This is the most commonly used option of hashing algorithms and whenever the password is converted into a specific pattern using this method it will be very simple to get the value through the Google system. In this case, there will be no chance of any kind of problem but unsuitability will be very high.
- SHA family of the algorithm: This was introduced in 1993 and has been compromised many times which is the main reason that organizations have been successful in terms of launching further methods associated with SHA and further SHA1, 2, and 3 are very easily available in the industry which the organization can implement whenever they are interested to become serious about the element of security.
- RIPEMD family of algorithms: This will be very well standing for race integrity primitives evaluation Message Direct and further this is very well based upon developing the applications with confidence. Since the output length in this particular case will keep on increasing, subsequent versions will be definitely helpful in providing people with an appropriate level of security coverage without any problem at any point of time throughout the process.
Hence, It is very important for the organization to note that the hashing algorithm element is very secure but will never be making it immune to attackers. At times the hacker will have the opportunity to provide input to the basic functions which can be further used for authentication, the best possible opportunity to make the applications immune to attacks will be to introduce the runtime application self-protection system so that everything will be done in the real-time without any problem. Since there will be limited human intervention in the whole process, the smart analysis will be very well carried out and the context will be the behaviour of the applications will be very well improved without any problem. This will be definitely helpful in making sure that things will be proficiently sorted out and further getting in touch with the experts at Appsealing can be considered as a good approach so that everything will be streamlined without any problem. Ultimately with the help of this scenario, organisations will be able to launch the perfect applications without any hassle at any point in time
